12Port Zero Trust Platform
12Port brings PAM, session auditing, Vault secrets, and East-West segmentation into a unified security platform.
12Port is a Zero Trust platform for Privileged Access Management and Microsegmentation. It simplifies elements of Zero Trust for enterprise security by unifying privileged access, credential vaulting, just-in-time (JIT) session control, and network segmentation for critical systems.
Deploy anywhere, activate only what you need, and centralize everything in one secure software platform—so you can reduce risk, improve security, and meet compliance requirements with ease.
12Port Zero Trust Platform
Deploy Fast. Scale Confidently.
12Port is built for rapid deployment, low operational overhead, long-term scalability, and affordable whether you are a small company or an enterprise with 100,000 employees. Get up and running fast, without security trade-offs.
- Agentless deployment.
- Cloud or on-premises with embedded or external database options for data sovereignty.
- Automated setup and updates in under 5 minutes.
- High availability architecture with peer nodes for isolated networks and scalability.
- Load balancing and multi-node support for distributed infrastructures.
- Multi-Tenant for Managed Service Providers
12Port Zero Trust Platform
Activate the 12Port Modules You Need
Deploy the right Zero Trust security capabilities when your business needs them without switching platforms. Minimize your attack surfaces, enhance your security posture, and ensure continuous compliance with evolving regulations.
- Privileged Access Management (PAM) –Secure, monitor, and manage access to privileged system, credentials, sessions, and rotate credentials, all in one integrated platform
- Credential Vault – Securely manage and share privileged credentials, passwords, SSH keys, and secrets, minimizing credential breaches.
- Remote Access – Monitor and secure JIT remote access across with full recording and auditing for improved security and compliance.
- Credential Rotation – Control privileged accounts, automate credential and key rotation, and enforce reset policies to meet compliance requirements.
Microsegmentation
- Enforce microsegmentation and tag-based policies to prevent East-West lateral movement to reduce security risks and contain treats faster.
12Port Zero Trust Platform
Privileged Access Management (PAM)
12Port allows you to gain full visibility and control over access by privileged identities, including remote access, administrative logins, and external vendor sessions. Turn every privileged session into a controlled, auditable, and policy-enforced access point, protecting the most sensitive areas of your infrastructure.
- Launch web-based or native client sessions through secure gateways.
- Enforce multi-factor authentication (MFA) before each session to verify user identity.
- Record sessions or monitor live activity, including keyboard input, clipboard usage, and file transfers.
- Assign access profiles by user, group, or asset with inheritance and override options.
Route sessions through peer nodes for secure access to isolated networks.
12Port Zero Trust Platform
Credential Vault
Centralize the management of passwords, tokens, and SSH keys across your environment with secure, auditable access controls. Keep sensitive secrets protected, compliant, and aligned with operational policies.
- Military grade a FIPS 140-3 validated cryptographic module.
- Secure passwords, credentials, and SSH keys; all fully encrypted.
- Enforce password complexity and SSH key standards by user, asset, or space(site).
- Control access to secrets without exposing credentials to users.
- Configure policy driven workflows to control and grant auditable access to shared credentials and secrets.
12Port Zero Trust Platform
Credential Rotation
Automates the lifecycle of privileged accounts and secure your identities without manual work or policy gaps. Give teams the tools to operate securely while enforcing the policies that protect critical systems.
- Automated password resets for known shared accounts.
- Shadow account support for privileged elevation without exposing credentials.
- Scheduled or event-based credential rotation.
- Job execution and reporting across remote systems, peer nodes, and task libraries.
- Support for Unix, Linux, Windows, AD, Entra ID, IBM i, Oracle Solaris, and more.
12Port Zero Trust Platform
Microsegmentation
Horizon enforces zero-trust policies across lateral East-West traffic by controlling how assets communicate internally. It helps reduce lateral movement and insider threats without disrupting existing infrastructure.
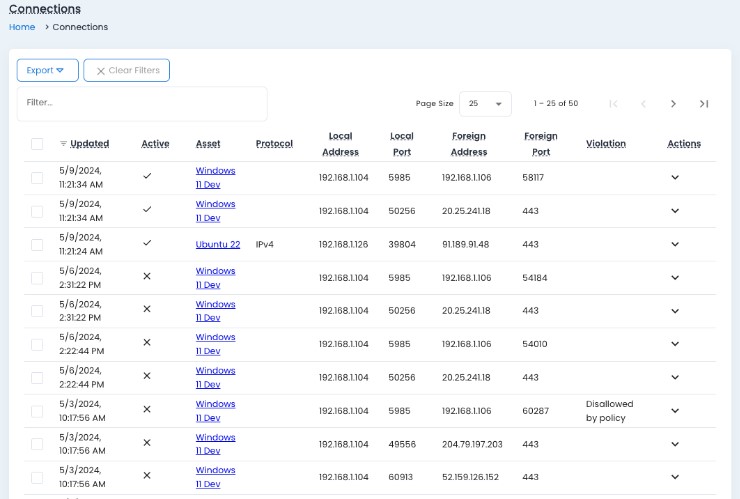
- Visualize all connections with interactive asset maps.
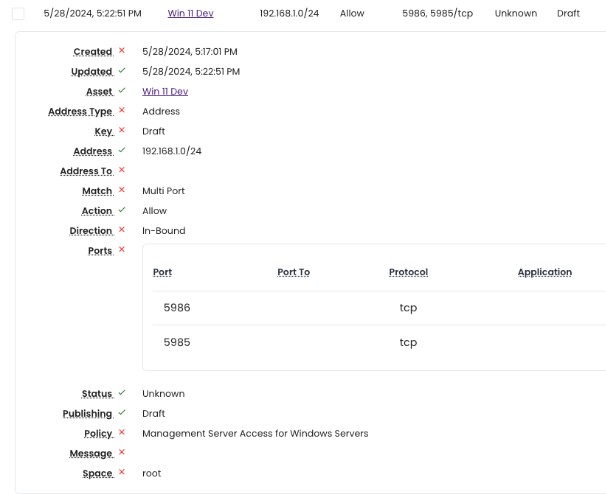
- Apply tag-based segmentation rules using actual asset data.
- Generate and publish native firewall rules to endpoints.
- Monitor segmentation policies in monitor-only mode before enforcing.
- Suggest optimized policies using analytical models and asset tags.
Benefits of the 12Port Zero Trust Platform
Unified Identity, MFA, and Access Control
Centralize your user management and enforce strong authentication across all 12Port modules. Ensure every user, session, and policy aligns with your security and organizational requirements.
- Integrate user authentication with SSO, LDAP, Active Directory, Entra ID, or use embedded directories.
- Apply MFA via TOTP, HOTP (Yubikey), email, Duo Security, or RADIUS solutions.
- Support for multi-tenancy and spacespace(site)-based hierarchy with inheritance and overrides for the most granular Role Based Access Controls (RBAC).
Intelligent Asset Management and Identity Import Automation
Simplify onboarding and policy creation with auto-tagging and rule-based organization. Manage asset sprawl efficiently without added complexity.
- Import assets from CSV, Active Directory, AWS, Azure, or VMware.
- Automatically tag assets and assign roles or policies.
- Use tags and asset types for fine-grained policy enforcement.
Deployment That Works with Your Infrastructure
12Port fits your architecture, no matter how distributed or complex. Flexible deployment options mean you can scale without retooling your stack.
- Support for interactive or headless deployments.
- Peer nodes for task execution and session routing in isolated networks.
- Built-in SSL management, service health checks, and diagnostics.
- Use embedded databases or integrate with your existing Oracle, SQL Server, MySQL, PostgreSQL, MariaDB, and cloud based databases.
Visibility, Audit Readiness and SIEM Integration
12Port is built for visibility and accountability at every layer. Stay audit-ready and improve incident response with full transparency.
- Real-time logging across sessions, secrets, jobs, and policies.
- Native SIEM integration for centralized monitoring and alerting.
- Detailed reporting at the asset, container, and space(site) level.
- System diagnostics and usage data for space(site) admins.
One Zero Trust Platform. Full Control.
The 12Port Zero Trust Platform unifies privileged access, secrets management, and internal network control s into one scalable, modular solution making it easier to implement a Zero Trust Architecture.
With 12Port, you get:
Agentless deployment and fast setup on Windows or Linux.
Session control and auditing for North-South privileged access.
Credential lifecycle management and secrets enforcement.
Zero trust microsegmentation from East-West traffic controls.
Scalable identity and access management with MFA.
Peer-node architecture for isolated networks and enterprise scalability.
SIEM-ready logs, audit trails, and reporting.
Whether you need to secure remote admin sessions, rotate sensitive credentials, or enforce lateral movement controls — 12Port gives you the tools, the flexibility, and the visibility to do it right.