What is Microsegmentation?
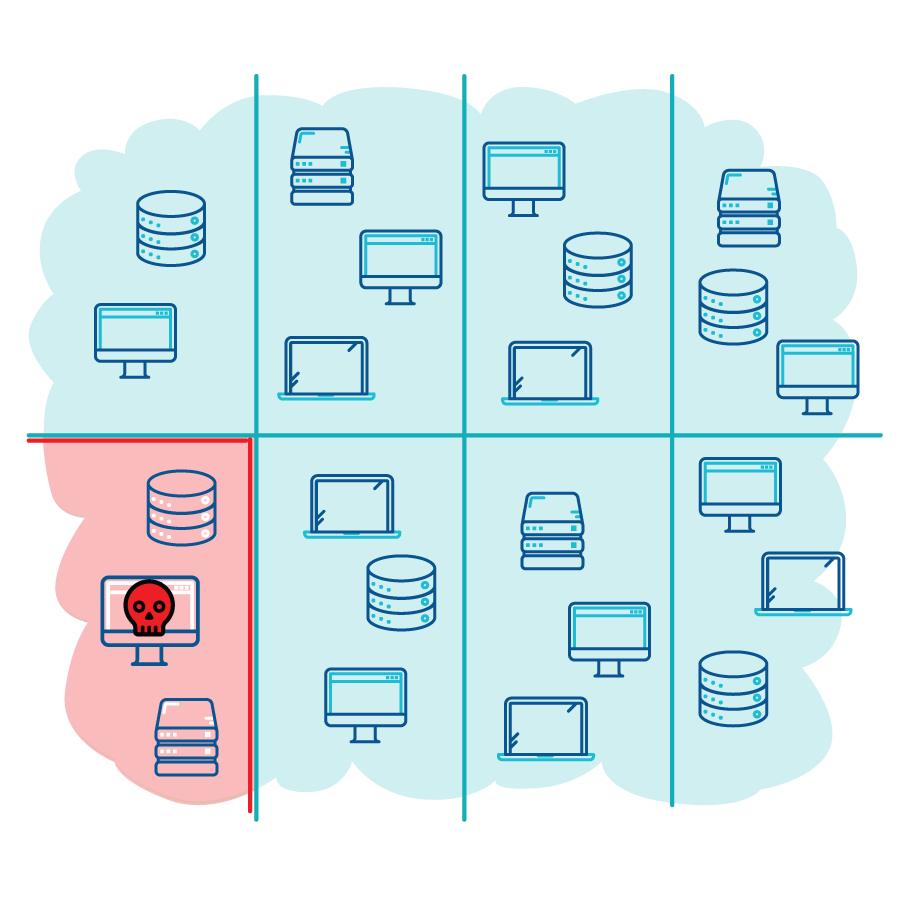
Microsegmentation is a security approach that divides a network into smaller, isolated segments, each with its own set of security policies. Unlike traditional segmentation, which divides broad sections of a network, microsegmentation operates at a much more granular level. This enables highly controlled access between applications, devices, or users within each segment, limiting unauthorized lateral movement and containing potential damage from attacks.
In cloud and virtualized environments, microsegmentation software creates secure zones around individual workloads, enabling customized, workload-specific policies down to the application level. This granular control is particularly beneficial in modern, multi-application cloud environments, where workloads on the same server or virtual machine can be isolated and protected individually.
Why You Need Microsegmentation?
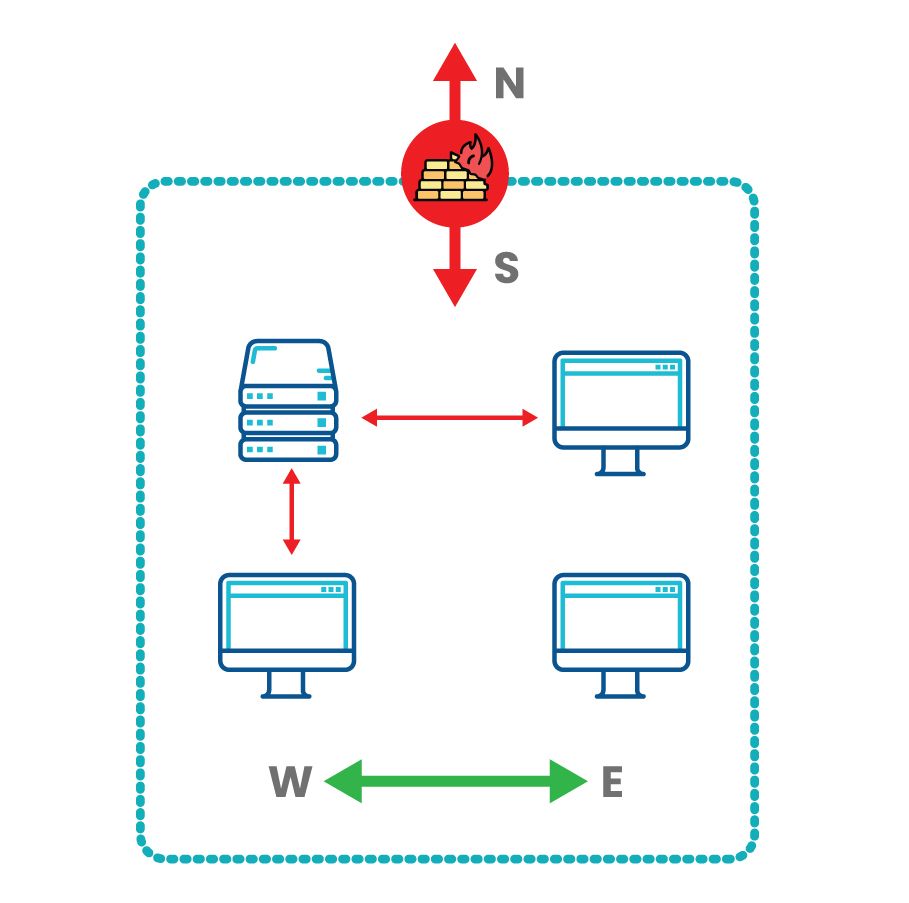
Most organizations rely on perimeter security solutions (firewalls) and identity access management (IAM) solutions (privilege access management and multifactor authentication), to inspect and control access to “north-south” traffic (client-to-server) that flows in and out of the network. These defenses implicitly trust “east-west” (workload-to-workload) traffic within the network, which often goes uninspected. However, with the rise of hybrid cloud environments, east-west communications now account for a significant portion of data traffic. Without proper visibility control over this traffic, traditional security tools leave a gap that attackers can exploit, enabling them to move laterally across workloads undetected.
Microsegmentation addresses this gap by providing isolation between individual workloads, creating granular access controls based on the principle of least privilege. Rather than merely creating reliable pathways, microsegmentation enforces security policies that determine if two endpoints should communicate, reducing the scope for lateral movement and effectively containing potential breaches.
Microsegmentation is tailored for east-west traffic within and between on-premises and cloud environments. By isolating workloads, it enables security teams to apply risk-based policies for inter-workload communications. This distributed and granular approach to policy enforcement strengthens east-west security and prevents lateral movement across your network and applications.
How It Works and Key Features
Microsegmentation leverages software to create secure zones within the network. Each zone has a set of customizable security policies dictating which systems or users can communicate with each other.
Key features of microsegmentation include:
- Flow Mapping and Visualization – Provides insights into north-south and east-west traffic patterns, allowing clear visualizations of network flows to help define precise security policies.
- Workload Isolation – Isolates individual workloads based on security policies, preventing lateral movement of threats across the network.
- Granular Policy Enforcement – Enables customized rules for access control based on factors like application type and user identity, ensuring fine-tuned security.
- Deployment in Virtual and Cloud Environments – Supports virtualized and IaaS environments, allowing seamless integration and adaptability in cloud and hybrid infrastructures.
- Asset Database – Houses critical information such as asset details, credentials, metadata, classification tags and segmentation taxonomies.
- Visibility and Monitoring: Gain deep visibility into traffic patterns and potential vulnerabilities within each segment.
- Dynamic Adaptability: Automatically adjust security policies as network configurations or applications change.
How Microsegmentation Fits Into A Zero Trust Architecture
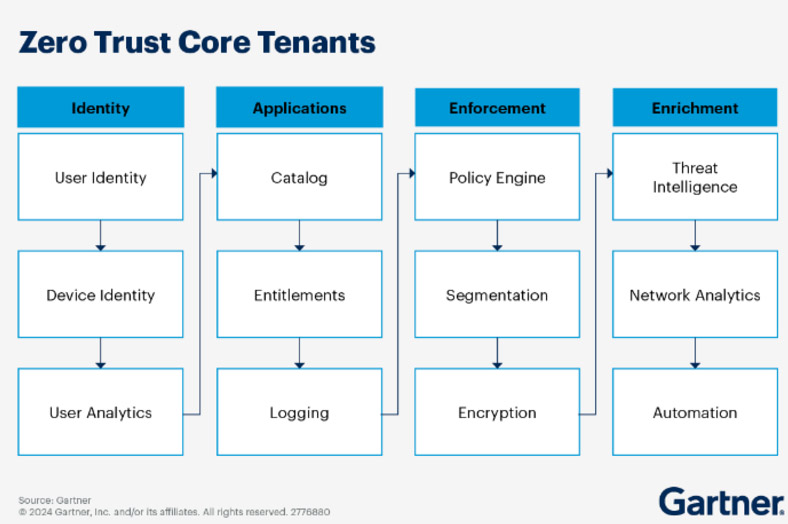
Microsegmentation is a foundational part of the Zero Trust security model, which is built on the principle of “never trust, always verify.” Zero Trust assumes that threats exist both inside and outside the network perimeter, so access should be restricted to the minimum required.
According to Gartner, microsegmentation is a particularly important concept in zero trust, as it is the ability to put a security service between any two workloads in your infrastructure, allowing you to isolate workloads and enforce access from end users to a workload or access from workload to workload.
- Least Privilege Access: Microsegmentation enables least privilege access, meaning users or applications only access what is essential.
- Enhanced Authentication and Access Control: Microsegmentation requires verification for all communications between network segments, aligning perfectly with Zero Trust principles.
- Containment of Potential Breaches: If a threat actor breaches one segment, microsegmentation prevents them from easily moving laterally, reducing potential damage.
Analysts at Forrester affirm that microsegmentation provides the necessary isolation and visibility that Zero Trust demands, creating strong, adaptable defenses within enterprise environments.
Benefits of Microsegmentation
Enhanced Security
Microsegmentation creates internal barriers that stop attackers from moving freely through the network. It improves defense against insider threats, blocking unauthorized access across critical systems. According to Gartner, “Microsegmentation can reduce the risk and impact of cyberattacks…if and when an attacker breaches the enterprise network.”
Reduced Breach Impact and Recovery Costs
By containing threats within individual segments, microsegmentation minimizes breach impact and reduces the cost of remediation. Companies with segmented networks and workloads experience significantly lower data loss and recovery expenses.
Improved Compliance and Audit Readiness
For industries governed by strict compliance standards (e.g., GDPR, HIPAA, PCI-DSS, NIST SP 800-207 and others), microsegmentation offers precise control over data flows. It allows businesses and federal government agencies (which are required to adopt a zero-trust architecture) to demonstrate compliance with strong security policies for sensitive information.
Operational Flexibility
Microsegmentation seamlessly scales across cloud, hybrid, and on-premises environments, making it suitable for diverse infrastructure setups. As IT ecosystems grow, microsegmentation adapts to new configurations, reducing complexity.
Use Cases for Microsegmentation
Microsegmentation doesn’t need to be complex with dozens and dozens of segmentations. Starting with simple microsegmentation projects—targeting the most critical or vulnerable areas—can deliver substantial network security benefits.
Cloud Segmentation
Microsegmentation divides cloud environments into secure, isolated zones, controlling and monitoring communication between different cloud resources and services. This helps prevent unauthorized access across cloud segments, ensuring compliance and security in hybrid or multi-cloud setups.
IoT Device Isolation
Microsegmentation enables the classification and isolation of IoT devices within networks, applying security policies that limit interactions based on device type and function. Suspicious or unidentified devices can be confined to restricted zones to mitigate risk.
Development and Production Isolation
By segmenting development, test, and production environments, organizations can ensure that data and processes in development do not inadvertently impact live operations.
API Security
By creating distinct network segments for API traffic, microsegmentation enforces strict access controls, allowing only approved endpoints to connect. This minimizes potential vulnerabilities and exposure of APIs to unauthorized users or threats.
Application Tier Segmentation
This use case focuses on safeguarding different layers of an application stack (e.g., web, application, and database tiers) to prevent intruders from laterally traversing within an application environment. It ensures that traffic between these layers is monitored and controlled through designated security zones.
Container Security
Using tools like Docker or Kubernetes, microsegmentation ensures containers operate within designated network boundaries and cannot access resources beyond their scope. This maintains container independence and prevents potential cross-container threats.
Industrial Control Systems (ICS) Protection
Microsegmentation enhances the security of operational technology (OT) and ICS by isolating individual programmable logic controllers (PLCs) and enforcing strict communication policies. This containment prevents lateral movement between sensitive devices within the same network.
Consider 12Port Horizon
The 12Port Horizon platform allows businesses to quickly and affordably segment network workloads. It can be deployed within your network in less than an hour, making zero trust security accessible for enterprises of all sizes.
Built on a secure, hierarchically partitioned asset database, 12Port Horizon offers intelligent tagging, role-based access, and object versioning for streamlined network traffic management. By leveraging native operating system firewalls and remote process execution scripts (SSH and PowerShell), the solution ensures efficient and secure traffic control.
Ready to get started with microsegmentation? Download a free trial today or schedule a personalized demo.