Policies
Dynamic virtual segment. Selector, Service, Source. Wildcard configuration. Policy preview. Traffic Visualization.
Policies
Dynamic virtual segments
Microsegmentation policies utilize tags from a segmentation taxonomy to designate assets for protection and determine which assets can access services. This tag-based policy continuously monitors changes in asset tags within the database to adjust access rules across the physical network. This dynamic mechanism effectively partitions distributed networks into isolated virtual segments aligned with both business and technical asset usage.
Policies
Selector, Service, Source
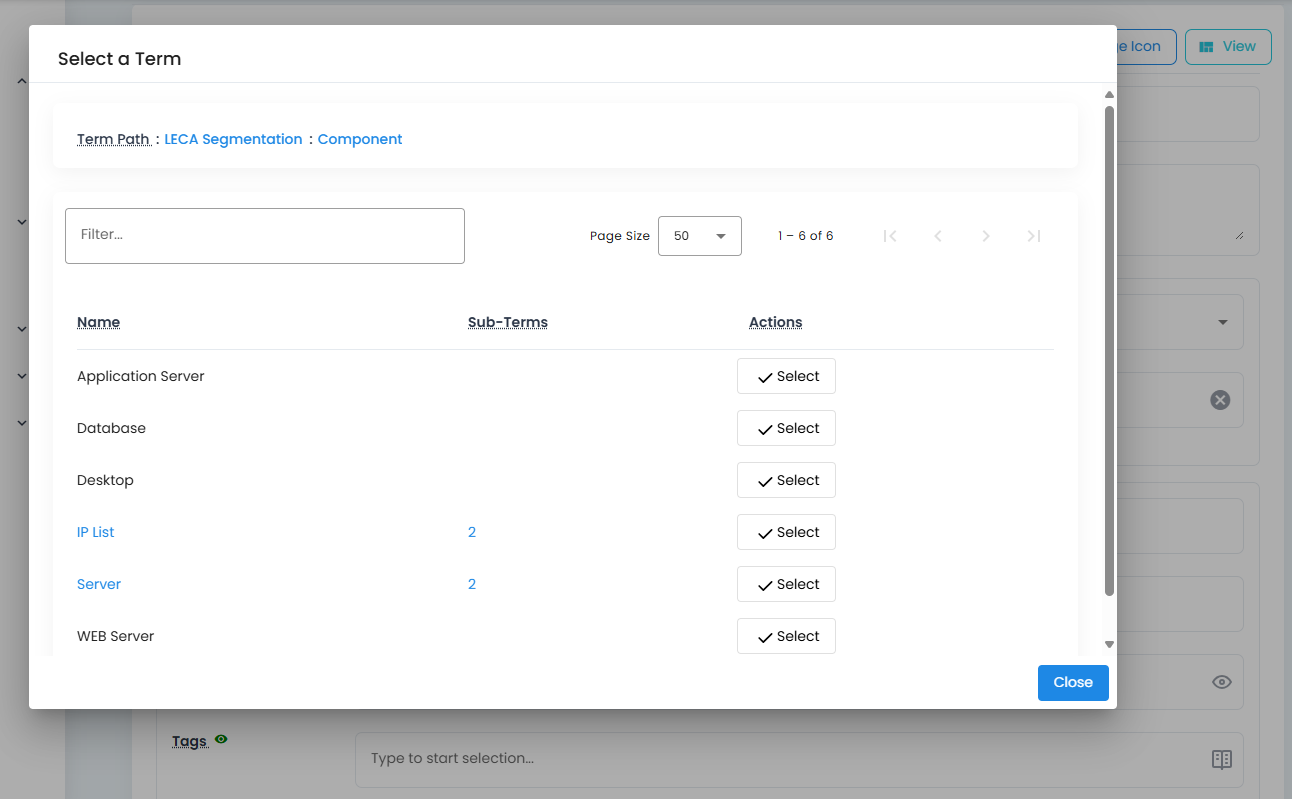
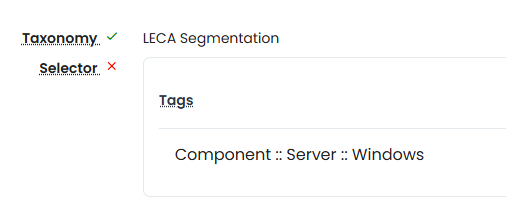
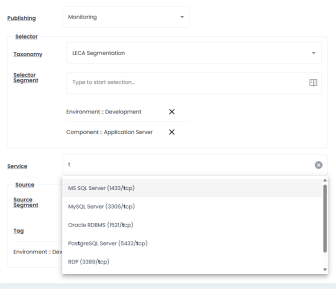
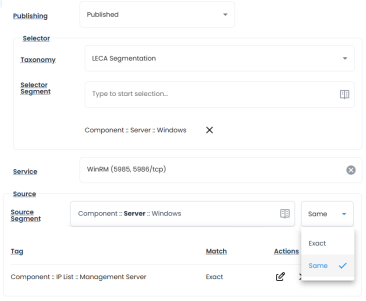
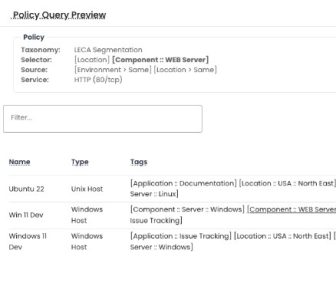
The building blocks of microsegmentation policy construction are the selector, service, and source. The selector comprises multiple tags used by the software to identify assets to which the policy applies. The service defines the network protocol and port affecting the workload, while the source includes tags that specify the range of clients permitted to connect to the service on the selected asset, which can be a network device or an IP range.
Policies
Wildcard configuration
Microsegmentation policies can utilize wildcard notation for defining the policy source, which helps streamline policy management while maintaining robust segmentation strategies.
For instance, a policy could allow connectivity to a specific asset from any asset within the same geographical location, application type (e.g., Content Management, ERP, or Process Control), and environment (development, staging, or production).
Policies
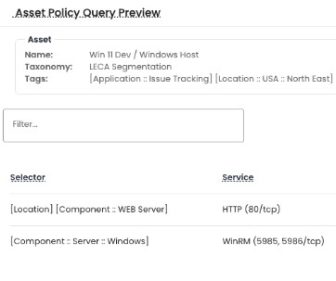
Policy Preview
Policy Preview is a graphical tool specifically designed to visualize the internal logic and application of policies. It queries the asset database to showcase the selected target's selector and source assets, enabling evaluation of policies before deploying them in production.
Policies
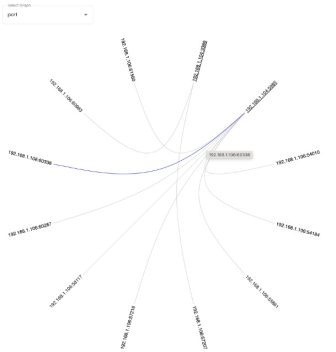
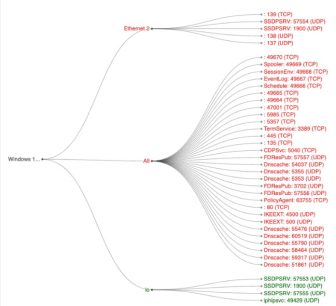
Traffic Visualization
A visual workload diagram constructed from endpoint data is a powerful tool for policy design and understanding the impact of policy implementations. It visualizes network traffic based on endpoint data, offering insights into policy application effectiveness and detecting policy violations.