12Port Credential Vault
Secure Credential Storage with Change Control and Role Based Access Control, Built for the Enterprise
Credential Vault stores your secrets and assets in using a military grade a FIPS 140-3 validated cryptographic module. The Credential Vault is the backbone of your 12Port platform, providing encrypted, structured, and policy-driven secret storage that adapts to any enterprise use case.
From passwords and keys to cloud credentials and configuration secrets, Vault empowers your security and IT teams with complete visibility, control, and automation.
12Port Credential Vault
Structure That Scales, Security That Sticks
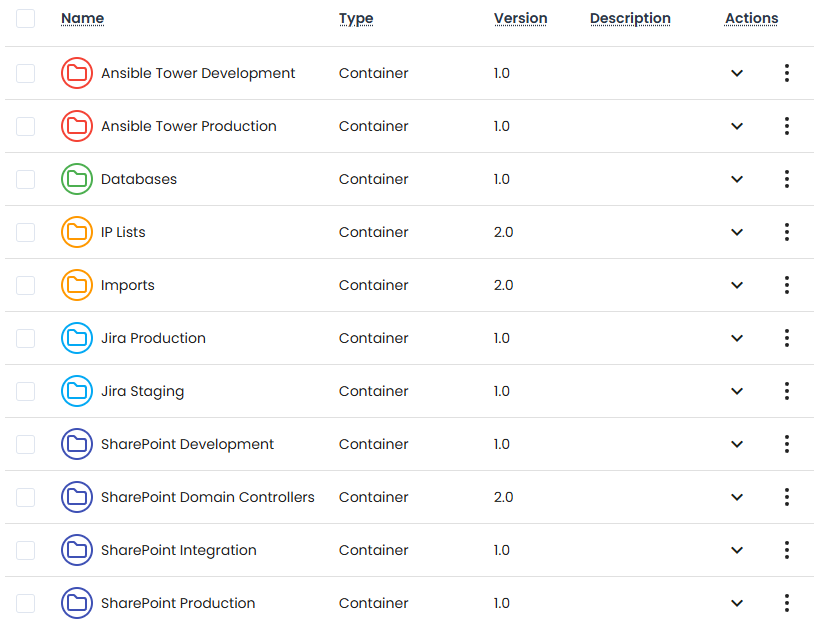
Traditional vaults fall short in dynamic environments. The 12Port Vault module introduces a container-based hierarchy that mirrors your organizational structure, whether by teams, systems, environments, or tenants.
Assets (secrets and credentials) can be organized in nested containers, reused across multiple contexts via linking, and managed at scale with consistent rules and access logic. You can even segment environments using multi-tenancy, supporting shared services in joint tenants and isolating client or team-specific assets in their own dedicated tenants.
Every secret is modeled using customizable asset types, letting you define exactly how each credential behaves, from field types and validation rules to icon inheritance and metadata. This flexibility supports real-world secrets like service accounts, database credentials, SSH keys, cloud access tokens, and many more.
12Port Credential Vault
Strongest Military Grade Encryption
The 12Port Platform uses a FIPS-140-3 Certified Module for all Vault functions (encryption at rest and in motion) ensuring you always have the strongest and approved encryption algorithms protecting your credentials and secrets.
12Port Credential Vault
Policy-Driven Access Workflows
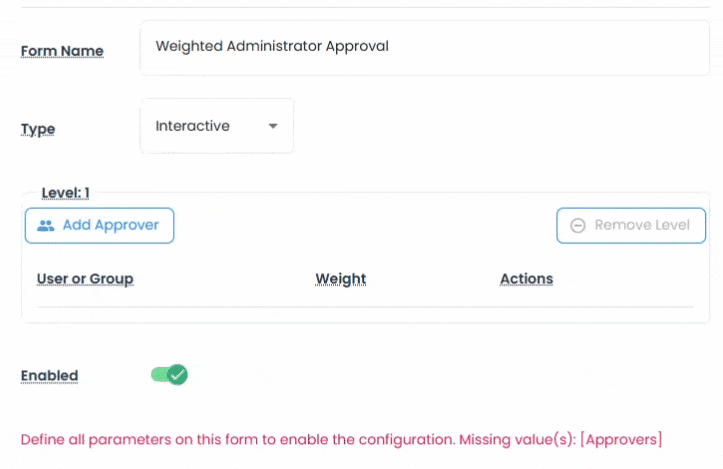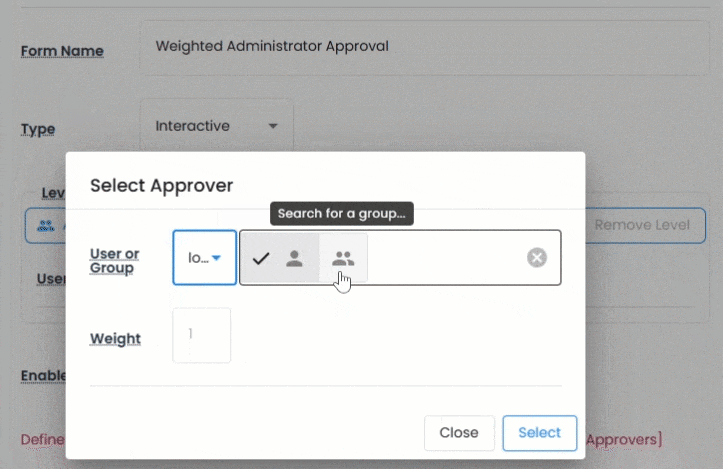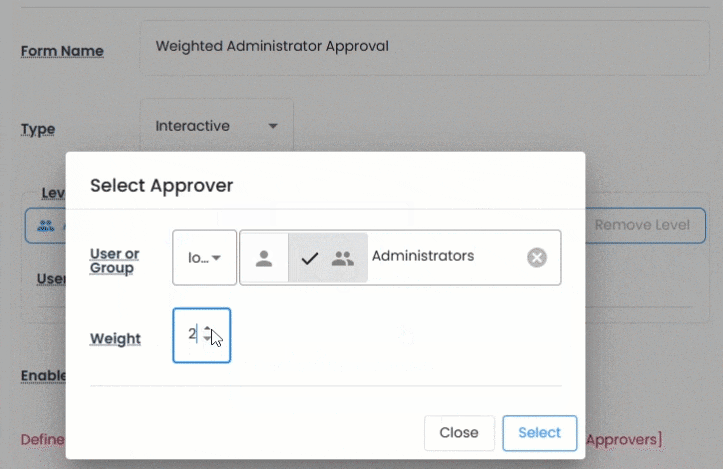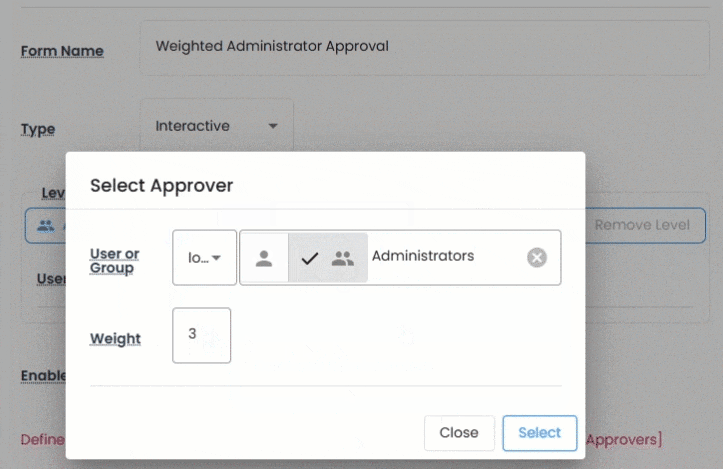
For secrets that require oversight, Vault includes a full workflow engine to control access through approval cycles.
Request forms are interactive, dynamic, and deeply customizable. You can define multi-level authorization, assign weighted approvers, and apply rules by spacespace(site), asset type, or time of access.
This ensures sensitive credentials are only accessed for legitimate business needs and that every request is tracked, audited, and reportable.
Users can track their own requests, approvals, and histories with intuitive reporting, while security teams maintain full visibility over who’s accessing what, and why.
12Port Credential Vault
Deep Access Control with RBAC for Secrets
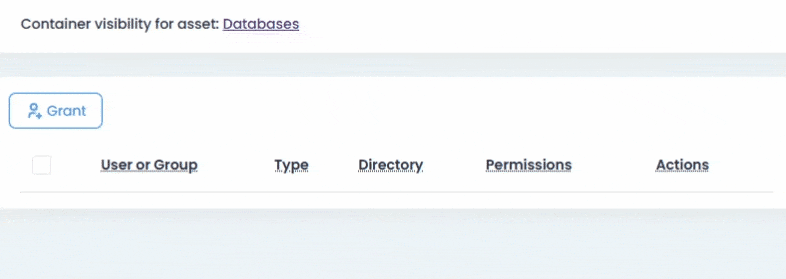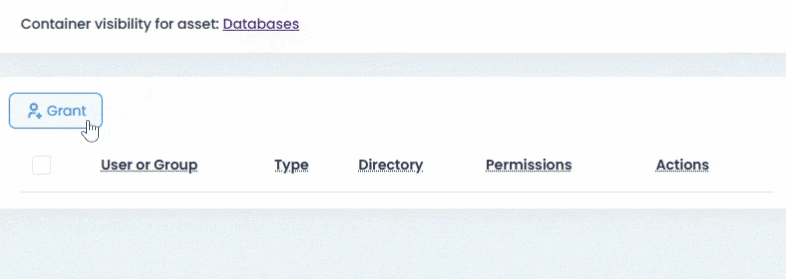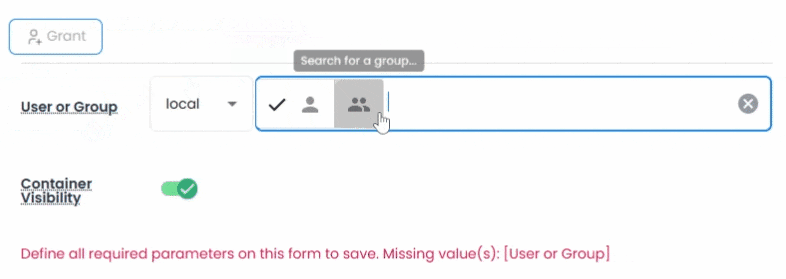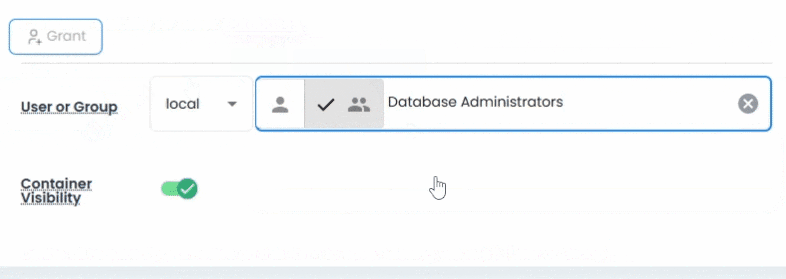
Vault doesn’t just store secrets it controls access to them. Using a layered role-based access control (RBAC) model, you can assign roles at the space(site), container, and asset levels.
Whether it’s a Space(Site) Administrator, Asset Manager, or simply a Viewer, each role carries specific, inheritable permissions. Field-level security lets you further encrypt sensitive fields and make them visible only through workflow-based approvals, ensuring credentials are only accessible with proper authorization.
Vault supports external identity providers out of the box, allowing you to grant permissions to users and groups from Active Directory, LDAP, Entra ID, or internal directories making it easy to enforce least-privilege access across hybrid environments.
12Port Credential Vault
Intelligent Tagging and Metadata-Driven Automation
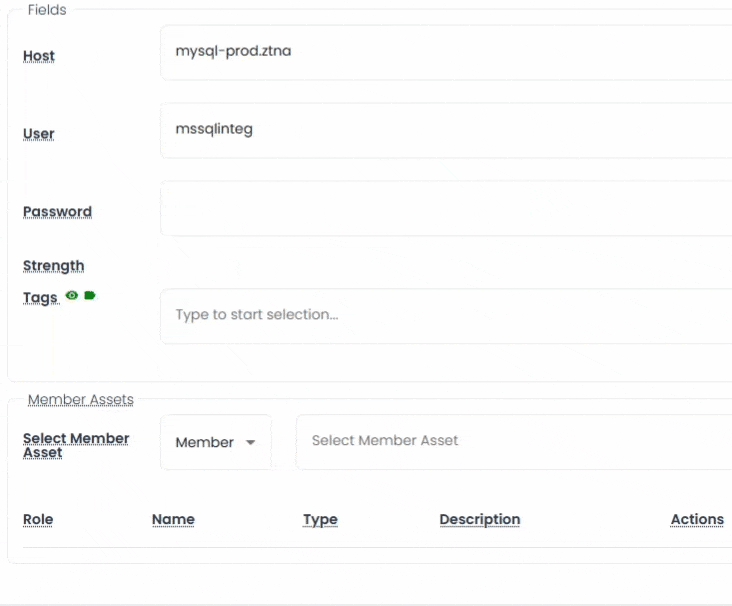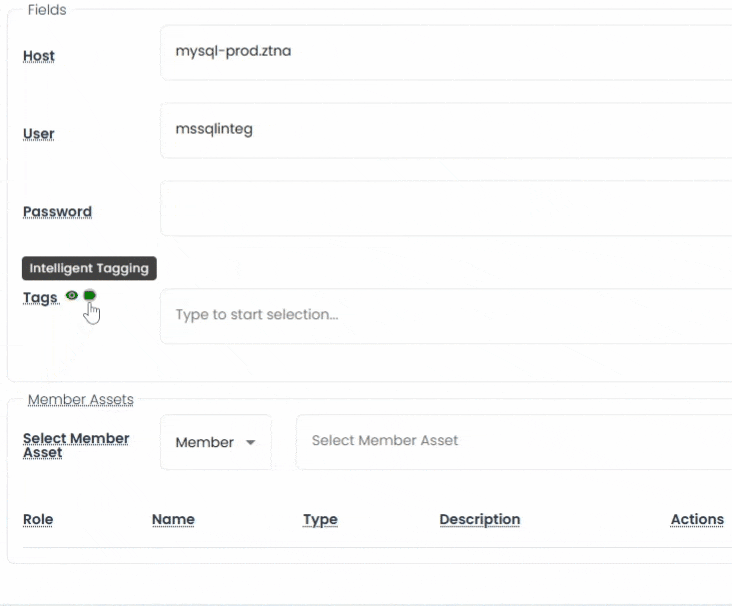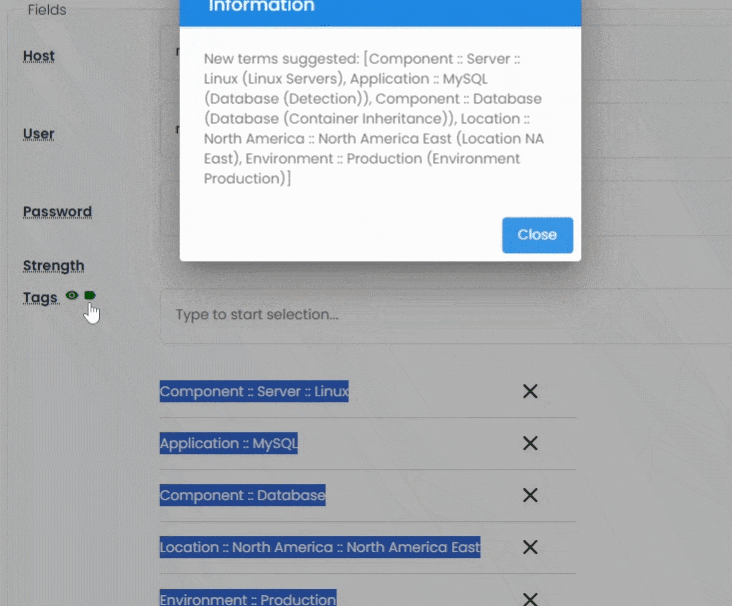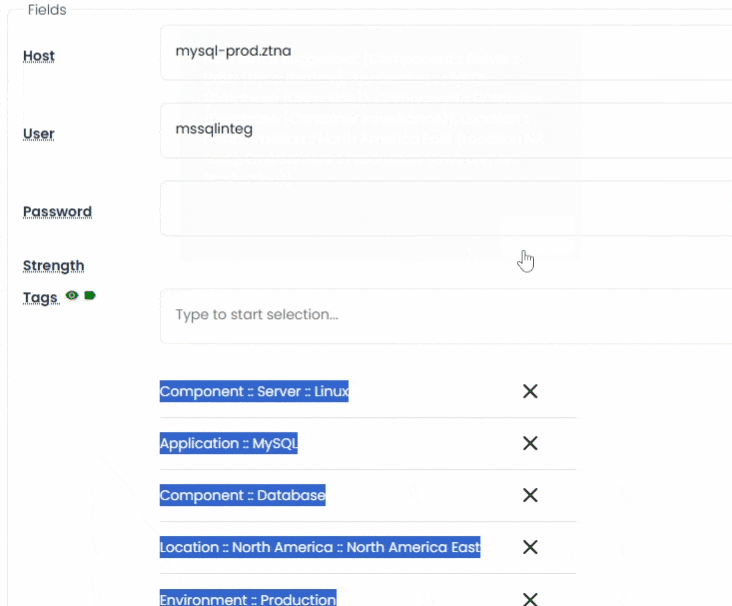
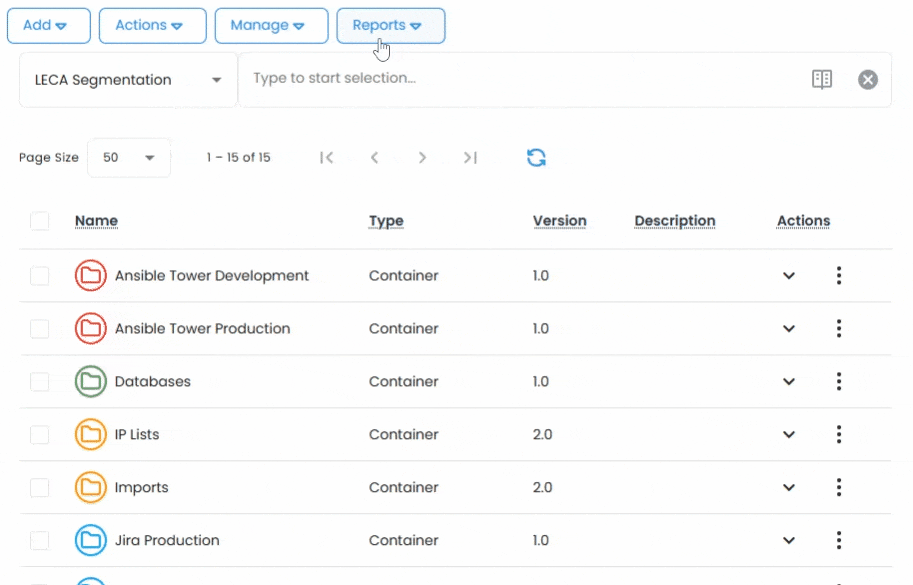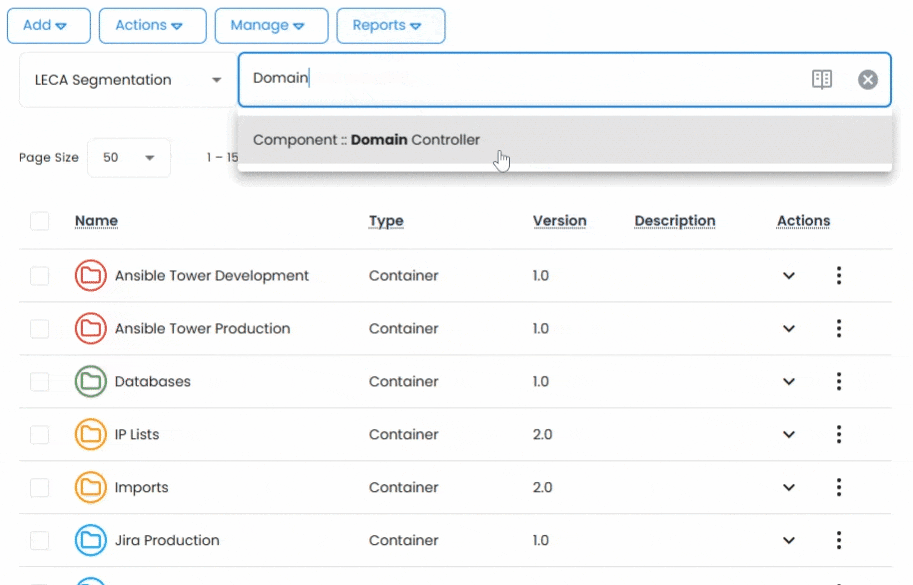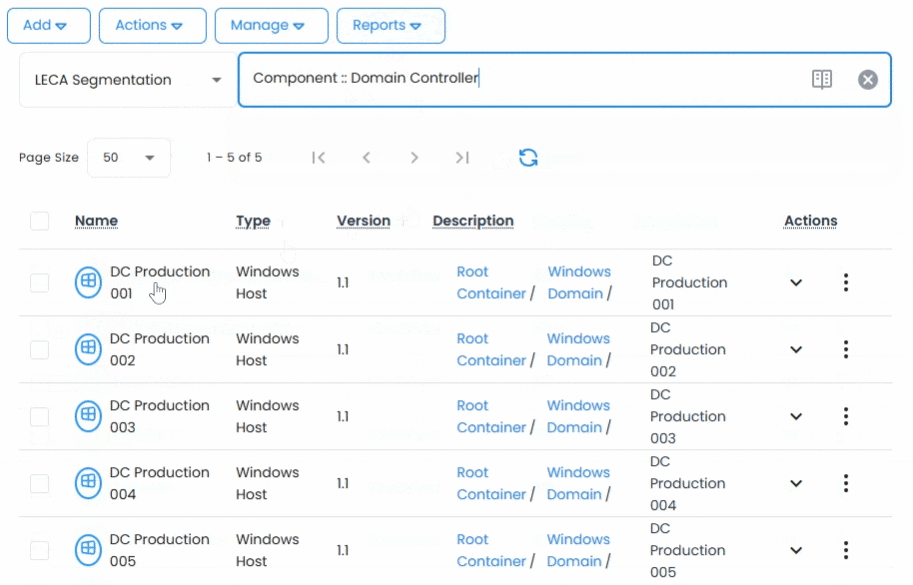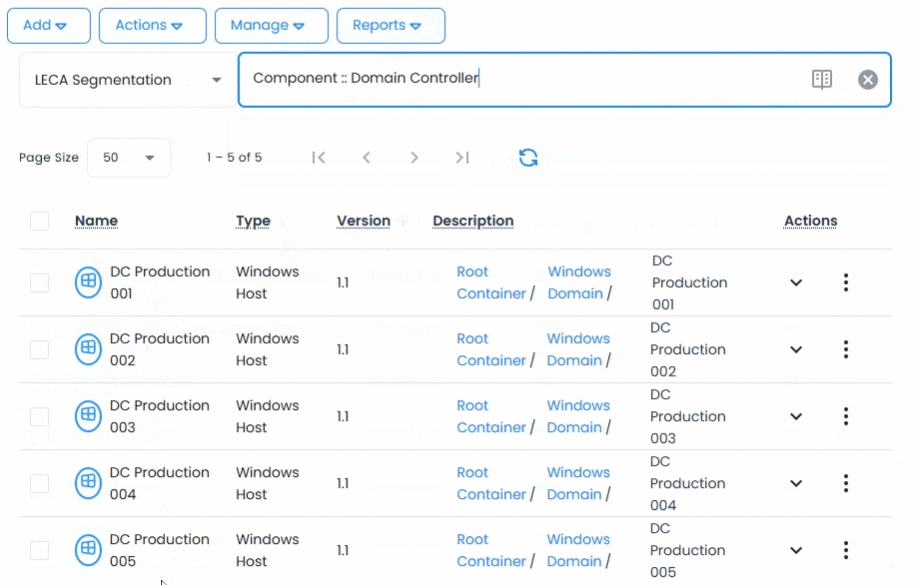
Organizing thousands of secrets doesn’t have to be manual. Vault includes a powerful auto-tagging engine that automatically classifies assets based on naming conventions, host metadata, or predefined rules.
Built-in taxonomy management lets you create hierarchical terms and synonyms to support structured classification. Whether you’re tagging by environment, owner, function, or sensitivity level, Vault ensures assets are always searchable and tagged with context-rich terms.
Tags can be applied during import, through bulk operations, or via interactive updates, helping you stay compliant and organized without the overhead.
12Port Credential Vault
Automate Secret Management at Scale
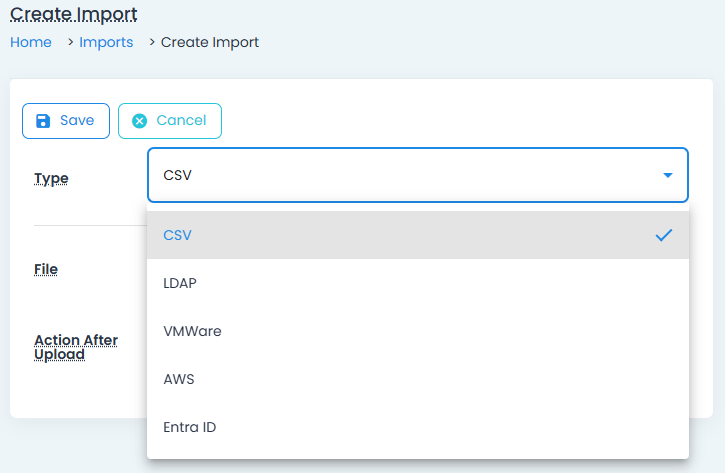
Vault makes it easy to scale your operations through mass management and automated imports. Secrets can be imported from:
- CSV files for bulk onboarding.
- Microsoft Active Directory for syncing accounts.
- AWS, Azure, and VMware environments using native query languages.
During import, Vault applies auto-tagging rules, enforces field policies, and integrates imported assets into your container and permission structure automatically. Mass operations like tagging, editing, deleting, or linking are just as fast, letting your team stay agile without compromising control.
12Port Credential Vault
Enterprise-Grade Search and Navigation
Even the best secrets management system is only as useful as its search engine. Vault gives you fast, powerful search capabilities, with full-text and metadata-based queries that make it easy to find exactly what you need, when you need it.
Use filters, taxonomy tags, asset types, or folder names to quickly locate secrets across environments. Built-in quick views, asset previews, and intuitive navigation minimize time-to-access and eliminate bottlenecks.
12Port Credential Vault
Developer-Friendly APIs and Customizable UI
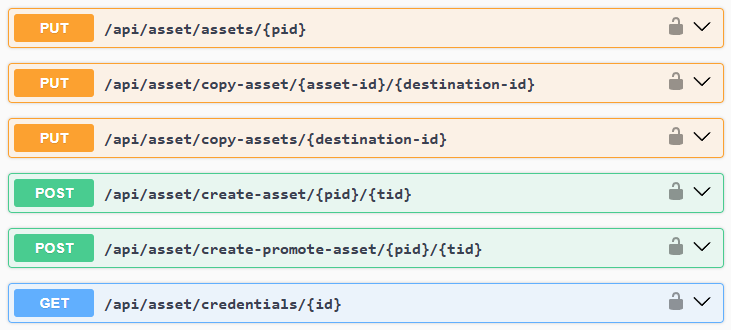
Whether you prefer automation or hands-on control, Vault supports both. The REST API, fully documented via OpenAPI, enables seamless integration with your existing CI/CD, IAM, or ITSM workflows.
For users, the modern web interface supports customizable layouts, themes, languages, and branding. Use vertical or horizontal navigation, switch languages, apply color schemes, and even brand the login page, ensuring consistency across teams and environments.
Vault also comes with a browser password autofill extensions for Chrome, Edge, and Firefox, enhancing usability for website login forms, without sacrificing control.
12Port Credential Vault
Full Audit Trails and Reporting
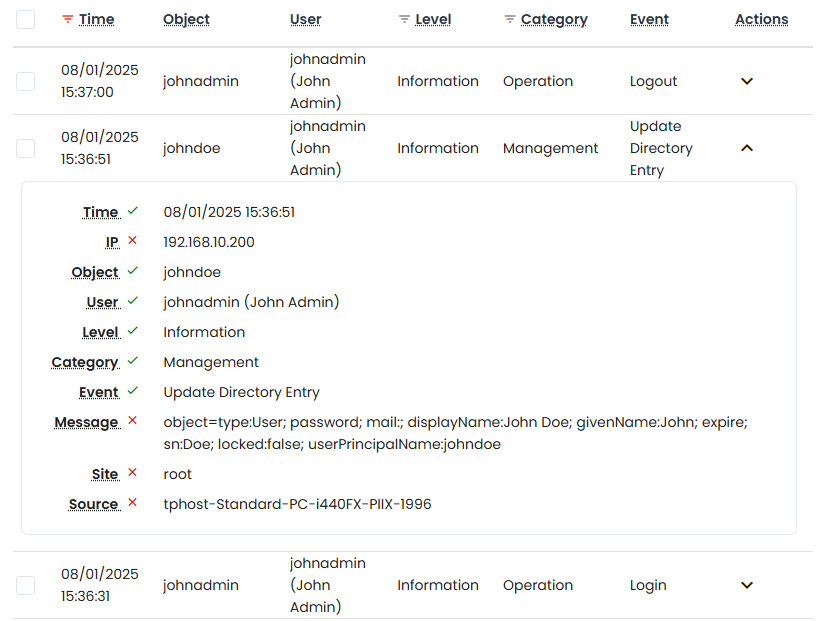
Compliance is built into Vault from the ground up. Every action, from login attempts to secret access, is fully logged, timestamped, user linked, and available in your audit trail.
Need a report? Use real-time filters to generate exportable views in CSV or PDF formats. Apply sorting, date ranges, and context filters to zero in on exactly what matters for your team, your auditors, or your customers.
Why Choose 12Port Credential Vault?
The Vault module isn’t just secure secret storage, it’s an enterprise-grade credential management system built for modern security, change control, governance, and scale.
With full RBAC enforcement, tagging automation, workflow approvals, and multi-tenant separation, Vault gives your organization the foundation it needs to securely manage privileged access, today and into the future.
Ready to See Vault in Action?
Vault is the backbone of secure, compliant access in complex IT environments. Schedule a live demo today and discover how it can help your team: