Cyber insurers are tightening requirements, raising premiums, and demanding proof that organizations can prevent credential misuse and contain lateral movement. In 2025, Privileged Access Management (PAM) has become one of the most decisive factors in whether a business can secure … Read More
Zero Trust

Insider Threats and the Power of Just-in-Time Privileged Access
September marks National Insider Threat Awareness Month, a reminder that some of the biggest security risks to an organization do not come from shadowy external hackers, but from the people already inside the walls. Employees, contractors, and trusted partners all … Read More

Privileged Access Management and Microsegmentation Are Better Together
Most cyberattacks today follow a predictable pattern. Attackers steal or abuse privileged credentials to gain access and then move laterally across systems to reach valuable data. Add to that the new risk from AI and agentic AI systems abusing credentials. … Read More

12 Questions to Ask a Zero Trust Solution Provider
Implementing Zero Trust is no longer optional. It’s a strategic imperative. But with a flood of solutions and vendors all claiming to be the answer, navigating your options can be overwhelming. Whether you’re just starting your evaluation or finalizing a … Read More

What’s New in 12Port Platform for Microsegmentation
At 12Port, we don’t wait for the “next big version.” Our 12Port Platform evolves every week. That means when you log in to manage your microsegmentation policies, you’re working with the most secure, most capable version of our software, always. … Read More
How to Segment SSH and RDP for Zero Trust Success
RDP and SSH remain top targets for attackers because they offer direct access to the systems that matter most. As covered in our earlier post (Why You Should Segment RDP & SSH), segmenting these high-risk protocols is one of the … Read More
The Role of Microsegmentation in Managing Lateral Movement Through Inbound and Outbound Traffic Policies
Microsegmentation has become a foundational component of enterprise security and a Zero Trust Architecture (ZTA). As threats continue to grow in complexity, the ability to contain and limit the spread of an attack inside the network is critical. Traditional perimeter-focused security … Read More

Why You Should Segment RDP & SSH
Securing remote access pathways often feels like an endless battle against evolving threats. Attackers continually search for exposed protocols, especially those that provide direct or near-direct access to critical systems. Remote Desktop Protocol (RDP) and Secure Shell (SSH) stand out … Read More
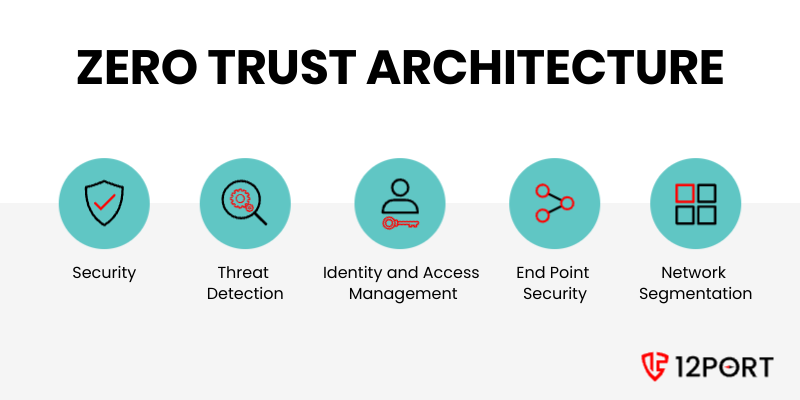
Importance of a Zero Trust Architecture
Zero Trust Architecture (ZTA) is more than a buzzword; it is an essential security framework used to combat escalating cybersecurity threats. Cybersecurity has become a non-negotiable priority in every organization’s infrastructure. Today, network security is not just about defending against … Read More

12Port Unveils New Microsegmentation Software at RSA Conference 2025
12Port Horizon simplifies microsegmentation, prevents lateral movement, and enhances zero trust security. EXTON, PA – April 7, 2025 – 12Port, a founder-owned and led cybersecurity startup, will debut its 12Port Horizon microsegmentation platform at RSA Conference 2025, April 28 – … Read More

