Microsegmentation has become a foundational component of enterprise security and a Zero Trust Architecture (ZTA). As threats continue to grow in complexity, the ability to contain and limit the spread of an attack inside the network is critical. Traditional perimeter-focused security … Read More
Network Security

Why You Should Segment RDP & SSH
Securing remote access pathways often feels like an endless battle against evolving threats. Attackers continually search for exposed protocols, especially those that provide direct or near-direct access to critical systems. Remote Desktop Protocol (RDP) and Secure Shell (SSH) stand out … Read More
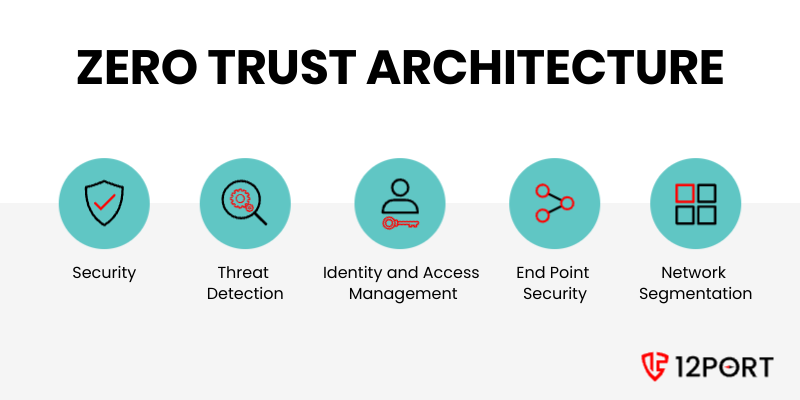
Importance of a Zero Trust Architecture
Zero Trust Architecture (ZTA) is more than a buzzword; it is an essential security framework used to combat escalating cybersecurity threats. Cybersecurity has become a non-negotiable priority in every organization’s infrastructure. Today, network security is not just about defending against … Read More

The Cost of Inaction in Cybersecurity
When it comes to cybersecurity, doing nothing is not a strategy—it’s a liability. Organizations must make an effort to improve their security posture continuously. While implementing robust security measures requires investment and effort, the cost of inaction (COI) can be … Read More

The Shift Toward Agentless Solutions in Modern Enterprise Network Security
Enterprise networks are constantly evolving, driven by innovations in technology and the increasing need for efficiency, scalability, and security. One key debate in this evolution is the role of agent-based software in securing on-premises servers and workstations. Historically, agents played … Read More

Importance of Dynamic Asset Classification in Microsegmentation
In this post, we explore the importance of dynamic asset classification in the context of microsegmentation. … Read More

Why Visualization is Essential in Microsegmentation
Microsegmentation is a powerful approach to securing network environments by creating smaller, isolated segments within a larger network. By doing so, it minimizes the attack surface and improves security across the network. However, understanding how traffic moves between these segments … Read More