Stolen identity and privileged access credentials account for 61% of all data breaches. And that number is growing year over year. Cybercrime groups, bad actors, and rogue insiders are now leveraging AI, making attacks faster, more targeted, and increasingly difficult … Read More
Cybersecurity
How to Enable MFA Before RDP and SSH Sessions
Remote access is essential for modern enterprises. IT administrators, DevOps teams, and vendors need to connect to critical infrastructure using Remote Desktop Protocol (RDP) or Secure Shell (SSH). But many organizations still allow these sessions without enforcing a critical security … Read More

Insider Threats and the Power of Just-in-Time Privileged Access
September marks National Insider Threat Awareness Month, a reminder that some of the biggest security risks to an organization do not come from shadowy external hackers, but from the people already inside the walls. Employees, contractors, and trusted partners all … Read More

12 Questions to Ask a Zero Trust Solution Provider
Implementing Zero Trust is no longer optional. It’s a strategic imperative. But with a flood of solutions and vendors all claiming to be the answer, navigating your options can be overwhelming. Whether you’re just starting your evaluation or finalizing a … Read More
The Role of Microsegmentation in Managing Lateral Movement Through Inbound and Outbound Traffic Policies
Microsegmentation has become a foundational component of enterprise security and a Zero Trust Architecture (ZTA). As threats continue to grow in complexity, the ability to contain and limit the spread of an attack inside the network is critical. Traditional perimeter-focused security … Read More

Why You Should Segment RDP & SSH
Securing remote access pathways often feels like an endless battle against evolving threats. Attackers continually search for exposed protocols, especially those that provide direct or near-direct access to critical systems. Remote Desktop Protocol (RDP) and Secure Shell (SSH) stand out … Read More
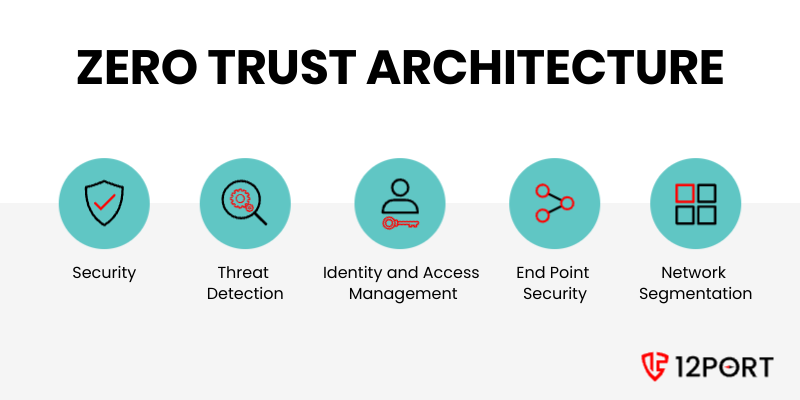
Importance of a Zero Trust Architecture
Zero Trust Architecture (ZTA) is more than a buzzword; it is an essential security framework used to combat escalating cybersecurity threats. Cybersecurity has become a non-negotiable priority in every organization’s infrastructure. Today, network security is not just about defending against … Read More

The Cost of Inaction in Cybersecurity
When it comes to cybersecurity, doing nothing is not a strategy—it’s a liability. Organizations must make an effort to improve their security posture continuously. While implementing robust security measures requires investment and effort, the cost of inaction (COI) can be … Read More

