Cyber insurers are tightening requirements, raising premiums, and demanding proof that organizations can prevent credential misuse and contain lateral movement. In 2025, Privileged Access Management (PAM) has become one of the most decisive factors in whether a business can secure … Read More

12 Questions to Ask Before Investing in a PAM Solution
Stolen identity and privileged access credentials account for 61% of all data breaches. And that number is growing year over year. Cybercrime groups, bad actors, and rogue insiders are now leveraging AI, making attacks faster, more targeted, and increasingly difficult … Read More
How to Enable MFA Before RDP and SSH Sessions
Remote access is essential for modern enterprises. IT administrators, DevOps teams, and vendors need to connect to critical infrastructure using Remote Desktop Protocol (RDP) or Secure Shell (SSH). But many organizations still allow these sessions without enforcing a critical security … Read More

Insider Threats and the Power of Just-in-Time Privileged Access
September marks National Insider Threat Awareness Month, a reminder that some of the biggest security risks to an organization do not come from shadowy external hackers, but from the people already inside the walls. Employees, contractors, and trusted partners all … Read More
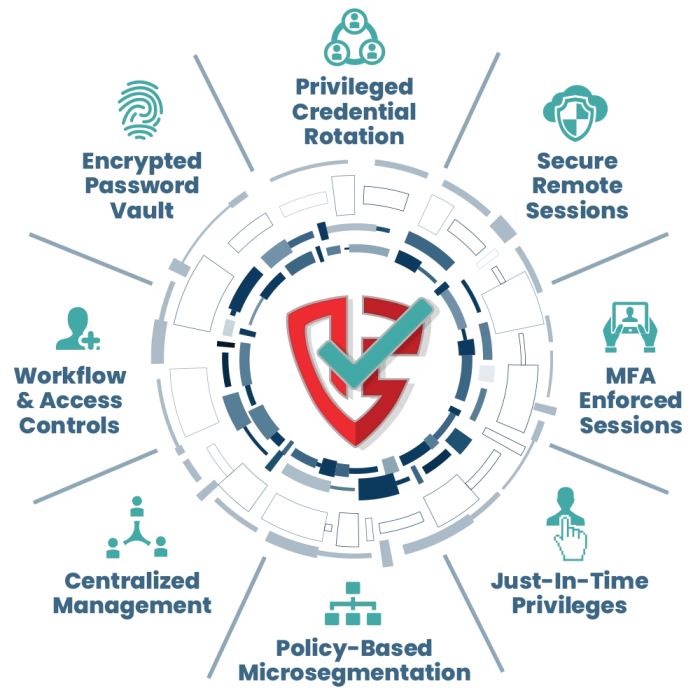
12Port Launches Agentless Zero Trust Platform with Privileged Access Management and Microsegmentation
Expanded platform secures privileged access and isolates workloads to block lateral movement, streamline compliance with HIPAA, PCI DSS, and NIST, and maximize ROI for IT and security teams. 12Port, a provider of enterprise-ready Zero Trust solutions, today announced expansion of … Read More
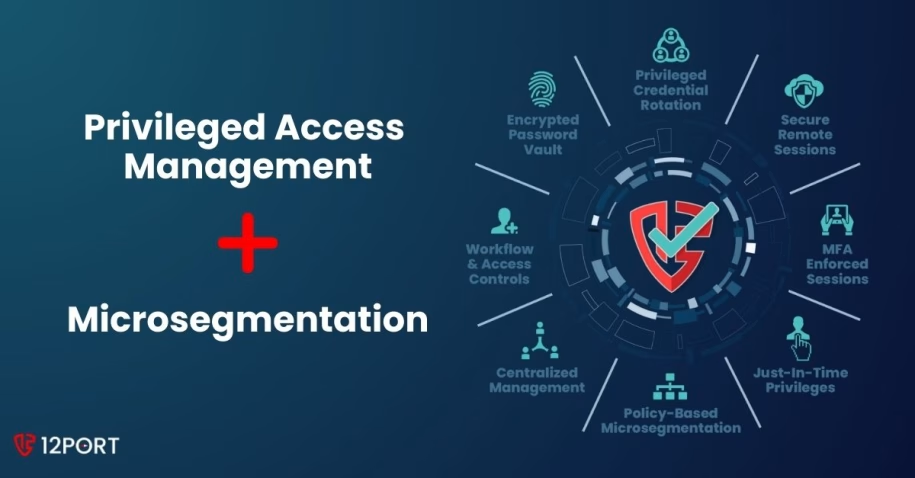
Privileged Access Management and Microsegmentation Are Better Together
Most cyberattacks today follow a predictable pattern. Attackers steal or abuse privileged credentials to gain access and then move laterally across systems to reach valuable data. Add to that the new risk from AI and agentic AI systems abusing credentials. … Read More

12 Questions to Ask a Zero Trust Solution Provider
Implementing Zero Trust is no longer optional. It’s a strategic imperative. But with a flood of solutions and vendors all claiming to be the answer, navigating your options can be overwhelming. Whether you’re just starting your evaluation or finalizing a … Read More

What’s New in 12Port Platform for Microsegmentation
At 12Port, we don’t wait for the “next big version.” Our 12Port Platform evolves every week. That means when you log in to manage your microsegmentation policies, you’re working with the most secure, most capable version of our software, always. … Read More
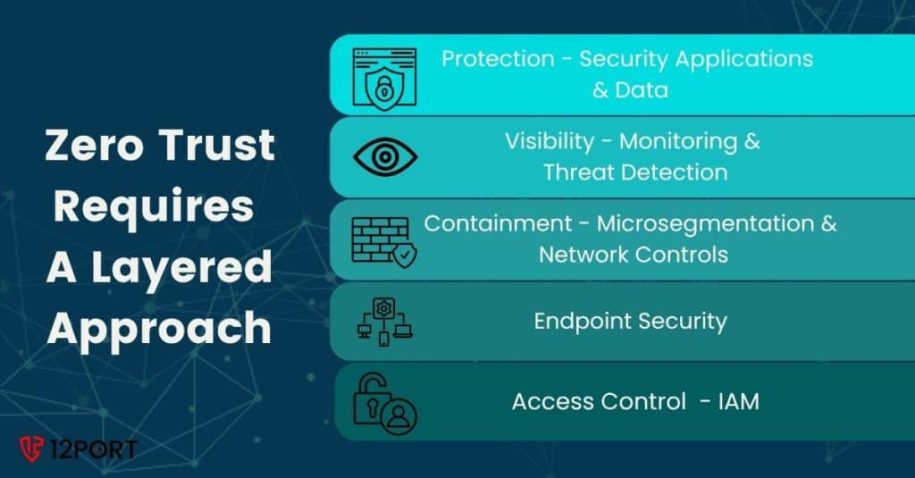
Why a Layered Approach Is Essential for Cybersecurity and Zero Trust
Today’s cybersecurity landscape is complex and unforgiving. Remote work, Saas, AI Agents, cloud migration, and ever-evolving cyber threats have exposed the limitations of relying on standalone security measures. To reduce risk, CISOs and IT leaders must embrace a layered cybersecurity … Read More

How to Segment SSH and RDP for Zero Trust Success
RDP and SSH remain top targets for attackers because they offer direct access to the systems that matter most. As covered in our earlier post (Why You Should Segment RDP & SSH), segmenting these high-risk protocols is one of the … Read More

